How to Protect a Website with Web Application Firewall | 1 Complete Guide about WAF
Protect Your Website with a Web Application Firewall: A Comprehensive Guide
In the rapidly evolving landscape of online threats, safeguarding your website against malicious attacks is paramount. Among the arsenal of cybersecurity tools available, a Web Application Firewall (WAF) stands as a stalwart defense mechanism, offering a crucial layer of protection for your web applications. This comprehensive guide aims to demystify the concept of WAFs, elucidating their significance, functionalities, implementation strategies, and best practices.
Understanding Web Application Firewalls
What is a WAF?
A Web Application Firewall (WAF) is a security solution designed to monitor, filter, and block HTTP/HTTPS traffic to and from a web application. Unlike traditional firewalls that primarily focus on network traffic, WAFs scrutinize and analyze the traffic specific to web applications, identifying and mitigating various forms of cyber threats.
Why Are WAFs Essential?
- Protection Against Common Threats: WAFs act as a shield, defending against a plethora of threats, including SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
- Mitigation of Vulnerabilities: They help patch vulnerabilities within web applications by filtering and inspecting incoming traffic, preventing exploitation of known weaknesses.
- Regulatory Compliance: Compliance with data protection regulations, such as PCI DSS and GDPR, often mandates the use of WAFs to ensure the security and privacy of sensitive information.
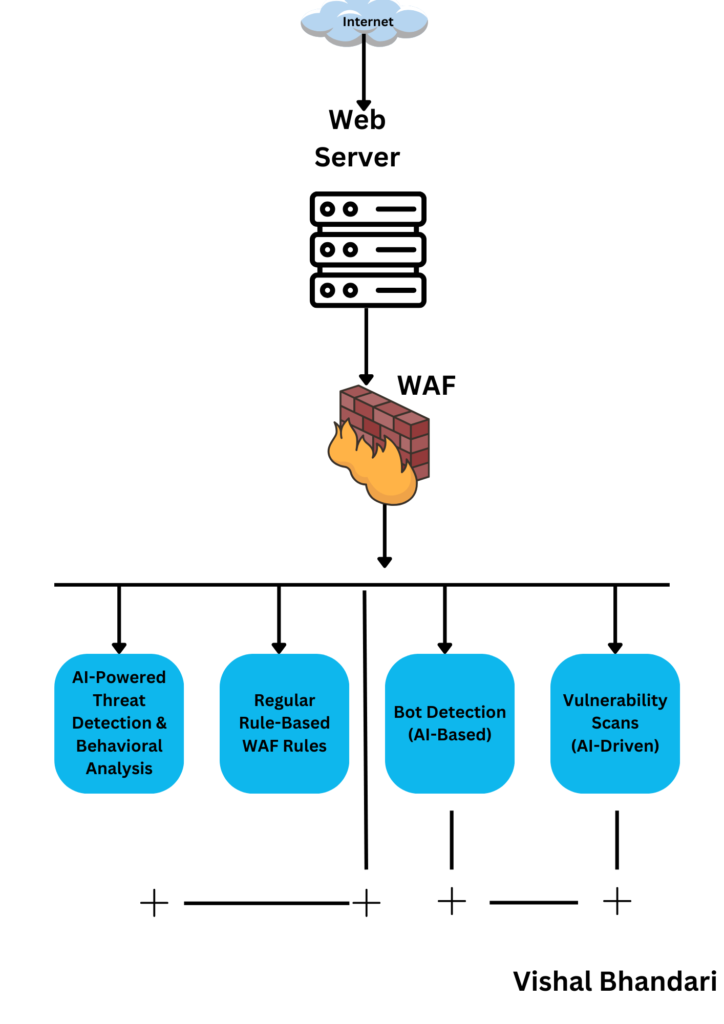
How Does a WAF Work?
Types of WAFs
- Network-based WAFs: Positioned between a website visitor and the web server, these inspect incoming traffic at the network level.
- Host-based WAFs: Installed directly on the server, these analyze traffic before it reaches the web application.
- Cloud-based WAFs: Operate remotely, providing scalability and accessibility while filtering traffic before it reaches the server.
Functionality
- Traffic Inspection: Analyzing incoming requests and responses for malicious patterns or signatures.
- Rule-Based Filtering: Implementing predefined rules or custom configurations to block or allow traffic.
- Logging and Monitoring: Recording traffic patterns and suspicious activities for analysis and auditing purposes.
- Real-time Protection: Instantly blocking potential threats without impacting legitimate traffic.
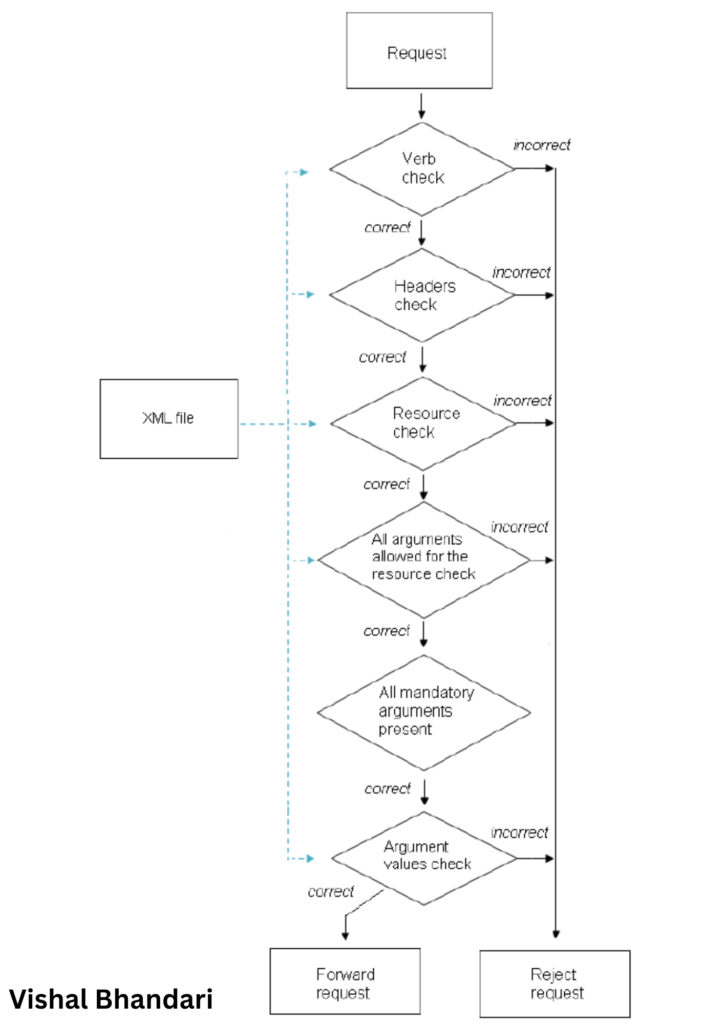
Implementing a WAF
Best Practices
- Identify Security Needs: Assess your web application’s vulnerabilities and specific security requirements.
- Choose the Right WAF: Select a WAF that aligns with your infrastructure, scalability, and customization needs.
- Configure Properly: Customize rules and settings to suit your application while avoiding unnecessary restrictions.
- Regular Updates and Maintenance: Keep the WAF updated with the latest security patches and configurations.
- Monitor and Analyze Traffic: Continuously review logs and traffic patterns to fine-tune security measures.
Challenges and Considerations
- False Positives/Negatives: Striking a balance between stringent security and not impeding legitimate traffic.
- Performance Impact: Ensuring that the WAF doesn’t slow down the application’s performance.
- Maintenance Overhead: Regular updates and configurations demand dedicated resources.
A Web Application Firewall serves as a critical component in fortifying your web applications against an ever-expanding array of cyber threats. By comprehensively analyzing and filtering incoming traffic, it acts as a proactive defense mechanism, reducing the risk of potential breaches, data theft, and service disruptions.
As the digital landscape continues to evolve, investing in a robust WAF and implementing it effectively is not just a best practice but a necessity to ensure the security and integrity of your online presence. Stay proactive, stay protected!
Remember, your website’s security is an ongoing commitment. Continuously assess and adapt your WAF strategies to combat emerging threats and keep your digital assets safe and secure.
Would you like more details on any specific aspect of web application firewalls, or is there anything else we can assist you with?
You Can Try our Other Tech Blogs Also:







