5 Types of Web Application Firewall (WAF) | Understanding Your Cybersecurity Shield
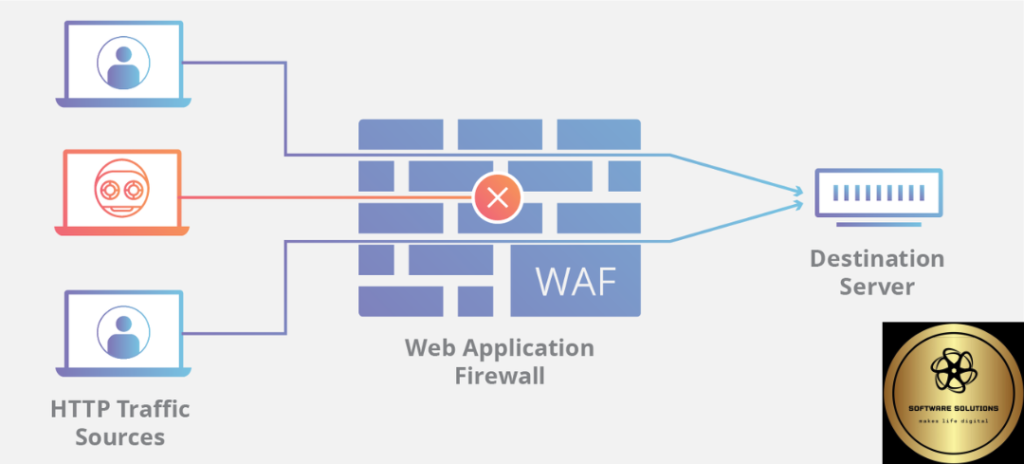
In the ever-evolving landscape of cybersecurity threats, businesses must be equipped with robust defense mechanisms to safeguard their digital assets. One critical component of a comprehensive cybersecurity strategy is a Wall Application Firewall (WAF), a specialized firewall that protects web applications from various forms of cyber attacks. With cyber threats becoming increasingly sophisticated, understanding the different types of WAFs available is essential for businesses to choose the most suitable solution for their needs. In this blog post, we’ll explore five types of WAFs and their functionalities.
1. Network-based WAF:
A network-based WAF operates at the network layer of the OSI model, inspecting traffic as it passes through the network perimeter. It analyzes incoming and outgoing traffic to identify and block malicious requests before they reach the web application server. Network-based WAFs employ techniques such as packet filtering, stateful inspection, and deep packet inspection to detect and mitigate various types of attacks, including SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
One of the key advantages of network-based WAFs is their ability to provide broad protection for all web applications hosted on a network, regardless of their programming language or platform. However, they may introduce latency due to the overhead of inspecting network traffic, and they may struggle to provide granular control over individual web application components.
2. Host-based WAF:
Unlike network-based WAFs, which operate at the network level, host-based WAFs are installed directly on the web application server. They function by intercepting requests before they reach the web server’s application layer, allowing them to inspect traffic at a deeper level. Host-based WAFs can analyze application-specific protocols and payloads, enabling them to detect and block attacks with greater precision.
Host-based WAFs offer several advantages, including low latency and the ability to provide granular control over web application traffic. Additionally, they can protect web applications running on different servers or platforms within the same network. However, managing and maintaining host-based WAFs can be more complex, as they require installation and configuration on each individual server.
3. Cloud-based WAF:
Cloud-based WAFs are hosted and managed by third-party service providers, who deploy them in the cloud and offer them to customers as a subscription-based service. These WAFs function by redirecting web traffic through their cloud infrastructure, where it is inspected and filtered before being forwarded to the origin server. Cloud-based WAFs leverage the scalability and resources of cloud computing to provide robust protection against a wide range of cyber threats.
One of the primary benefits of cloud-based WAFs is their ease of deployment and scalability. Since they are hosted in the cloud, there is no need for on-premises hardware or software installation, making them ideal for businesses with limited IT resources. Additionally, cloud-based WAFs can effectively mitigate large-scale DDoS attacks by distributing traffic across multiple servers and data centers.
4. Virtual WAF:
Virtual WAFs, also known as software-based WAFs, are deployed as virtual appliances within a virtualized environment. They function similarly to host-based WAFs but are designed to operate within virtualized infrastructure, such as virtual machines (VMs) or containers. Virtual WAFs provide the same level of protection as traditional WAFs but offer greater flexibility and scalability in terms of deployment.
One of the key advantages of virtual WAFs is their ability to scale dynamically to accommodate changes in web application traffic and workload. Since they are deployed as virtual appliances, they can be easily provisioned or decommissioned as needed, making them well-suited for dynamic or cloud-native environments. Additionally, virtual WAFs can be integrated seamlessly with existing virtualized infrastructure and security solutions.
5. API-based WAF:
As modern web applications increasingly rely on APIs (Application Programming Interfaces) to interact with external systems and services, protecting these APIs from cyber threats has become a critical concern. API-based WAFs are specifically designed to secure API endpoints and enforce security policies for API traffic. They inspect API requests and responses for signs of malicious activity, such as injection attacks or unauthorized access attempts, and block or allow them based on predefined rules.
API-based WAFs offer several advantages, including the ability to protect RESTful APIs, SOAP APIs, and other types of web services. They provide granular control over API traffic, allowing organizations to define security policies based on factors such as HTTP methods, headers, and payloads. Additionally, API-based WAFs can integrate with API management platforms and developer portals to streamline API security management.
Lastly, Wall Application Firewalls (WAFs) play a crucial role in protecting web applications from a wide range of cyber threats. By understanding the different types of WAFs available, businesses can choose the most suitable solution based on their specific requirements and infrastructure. Whether it’s a network-based WAF for broad network-level protection or a cloud-based WAF for scalable and cost-effective security, investing in the right WAF is essential for safeguarding digital assets and maintaining business continuity in today’s threat landscape.
Check our Other Tech Blogs
- How to Recover a Hacked Website
- How to protect a Website with Web Application Firewall
- What is VPN
- How to Secure Website with Artificial Intelligence
- Latest Research on DMZ
FAQs
Q. What is a Web Application Firewall (WAF)?
A. A WAF is a security solution designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the internet.
Q. What are the different types of Web Application Firewalls?
A. There are primarily two types: Network-based WAF and Host-based WAF. Network-based WAFs are deployed in front of web servers and protect multiple applications. Host-based WAFs run on the same server as the web application, providing more granular control.
Q. How does a Network-based WAF work?
A. Network-based WAFs inspect traffic before it reaches the web server. They analyze HTTP requests and responses to detect and block malicious activity based on predefined security rules.
Q. What are the advantages of Network-based WAFs?
A. Network-based WAFs offer centralized protection for multiple web applications, making them easier to manage. They can also be deployed in a reverse proxy mode to hide server IP addresses and mitigate DDoS attacks.
Q. What is a Host-based WAF?
A. Host-based WAFs are installed directly on the web server or within the application code. They provide more detailed insights into application behavior and can enforce security policies specific to individual applications.
Q. What are the benefits of Host-based WAFs?
A. Host-based WAFs offer deeper visibility into application traffic and behavior, allowing for more accurate threat detection and mitigation. They can also provide protection for applications that cannot be proxied through a network-based WAF.
Q. Are there any challenges associated with Host-based WAFs?
A. Host-based WAFs may introduce performance overhead on the web server and require additional configuration to ensure compatibility with specific applications. Additionally, they may have limitations in terms of scalability compared to network-based solutions.







